
A Computer’s Heat Could Divulge Top Secrets
A Computer’s Heat Could Divulge Top Secrets
June 18, 2015
Scientific American — The most secure computers in the world can’t “Google” a thing — they are disconnected from the Internet and all other networks. The U.S. military and the National Security Agency rely on this attack-prevention measure, known as air-gapping.
But where there’s a will, there’s a way: a team of BGU doctoral students led by Prof. Yuval Elovici, director of the BGU Cyber Security Research Center, announced it can obtain information from an air-gapped computer by reading messages encoded in the heat given off, like smoke signals, by its processors. The computer scientists call their hack BitWhisper.
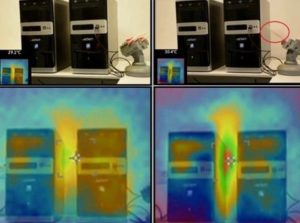
Two air-gapped PCs positioned in the parallel layout. Using BGU’s BitWhisper, the left computer transmits a command that instructs the right computer to calibrate and fire a USB game rocket.
BGU’s BitWhisper bridges the air-gap between the two computers, approximately 15 inches (40 cm) apart that are infected with malware by using their heat emissions and built-in thermal sensors to communicate.
It establishes a covert, bi-directional channel by emitting heat from one PC to the other in a controlled manner. By regulating the heat patterns, binary data is turned into thermal signals. In turn, the adjacent PC uses its built-in thermal sensors to measure the environmental changes. These changes are then sampled, processed, and converted into data.
The process is very time consuming. The compromised computers can transmit only a maximum of eight bits per hour and can be located no more than 16 inches apart. But that rate is enough to get what you need, says Yisroel Mirsky, a BGU doctoral student on the BitWhisper team.
“You need only about five bits,” says Mirsky, for a simple message, such as a command from the connected computer to the disconnected one, to initiate a data-destroying algorithm.



